Validate Authorization
User account actions over resources are tested against known policies using the Validate Authorization method. The context for the authorization is built from the user account's (the subject) JWT token or API Key.
**enforcer.validateAuthorization()** - given an intent to complete some action over a resource, test whether or not the user account defined by the current auth session has consent to complete the requested action. Uses the concept of Base Context and Derived Context to evaluate user accounts against Mesh API policies.
| Field | Description | Valid Values |
|---|---|---|
action | Validation requests must declare the action that the subject intends to make on the resource | read, write |
contexts | An arbitrary number of context requests offered by the Mesh API Admin | sharing_intents, id_sessions, account_groups, tenant, role |
policy_id | Policies are defined by Mesh Admins | app.mesh_sharing_intents, app.mesh_acl |
resource | The fully qualified resource identifier to locate the resource | Resource location path |
resource_type | The resource type | api, storj, sxt-table, sxt-view, object-store, vnft |
security_artifact | Optional base64 encoded security data (table biscuits, access grants). May be required for the sharing recipient to access the resource | Base64 encoded string |
| Context Type | Description | Valid Values |
|---|---|---|
sharing_intents | Context check for any sharing intents made for the subject's self, tenant, role, or account groups | N/A |
id_sessions | Context check for identity verification sessions (liveness checks) | N/A |
account_groups | Context check for groups that the subject belongs to | N/A |
tenant | Context check for subject's tenant | Public, Private |
role | Context check for the subject's role | Admin, Service Account, Developer, User |
import { initializeMeshSDK, logResponse } from "./util";
import {
ValidateAuthorizationResponse,
ValidateAuthorizationRequest
} from "@instruxi-io/mesh-sdk-core";
async function main() {
try {
const mesh = await initializeMeshSDK();
const request: ValidateAuthorizationRequest = {
action: "read",
contexts: [
"sharing_intents",
"account_groups",
"id_sessions"
],
policy_id: "app.sharing_intents",
resource: "sj://0x92F78491093bA0dd88A419b1BF07aeb3BA9fD0dc/file.json",
resource_type: "file"
};
let response: ValidateAuthorizationResponse = await mesh.enforcer.validateAuthorization(request);
await logResponse('Authorization Validation', response);
} catch (error) {
console.error("An error occurred:", error);
}
}
main().catch((error) => {
console.error("Unhandled error in main function:", error);
process.exit(1);
});Example of validation logic
Concept Check
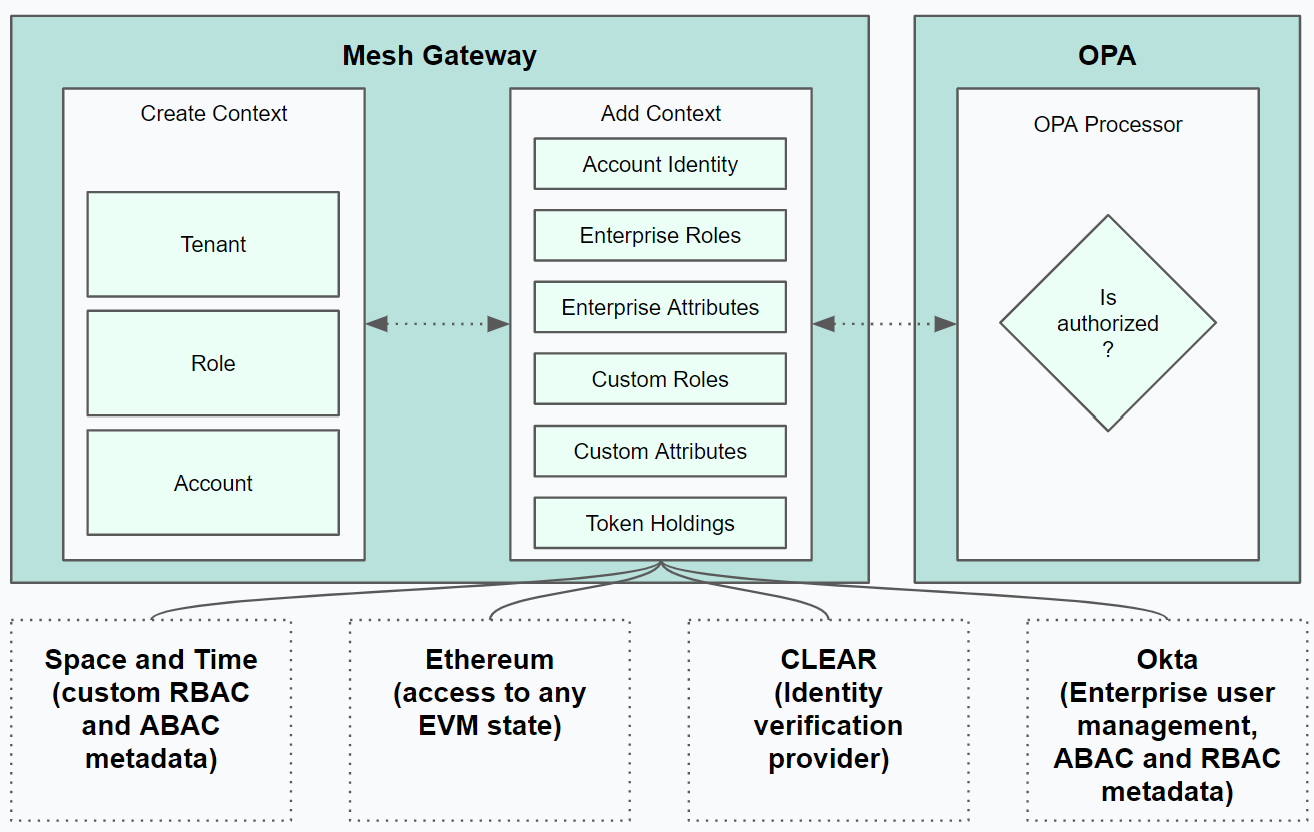
- User Account Context - The user context in the Mesh API web server is defined by user account metadata. The user account's metadata is sourced from the application database (base context) from admin defined master data tables built for the web application. The
- Base Account Context - On Mesh API, the user account's Base Account Context is the Account Address, Tenant, and Role sourced from the application database in Space and Time.
- Derived Account Context - The Validate Authorization capability on the Enforcer allows clients to test custom authorization requests on the Mesh API by specifying additional contexts. The Enforcer is capable of Deriving additional context from metadata sourced from secondary sources of account data using the Base Context as inputs to fetch new data.
- Open Policy Agent (OPA) - OPA offers a processing environment to evaluate policies written as
Reguagainst account context
Updated 6 months ago
